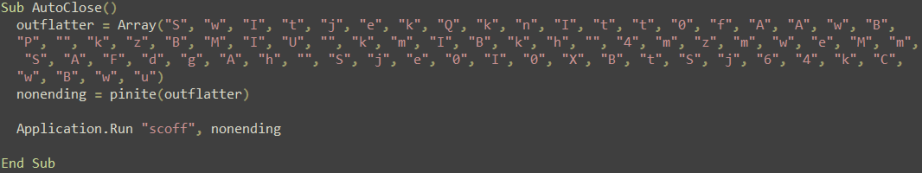
A user received malspam with a .doc attachment. Static analysis of the file showed it was a Microsoft Word 2007+ document with an embedded macro located in vbaProject.bin.
The malware authors trick victims into enabling macros (Enable Content) and, to better evade sandboxes, use AutoClose to execute the macro after the file has been closed.

Image file from the document
Example:
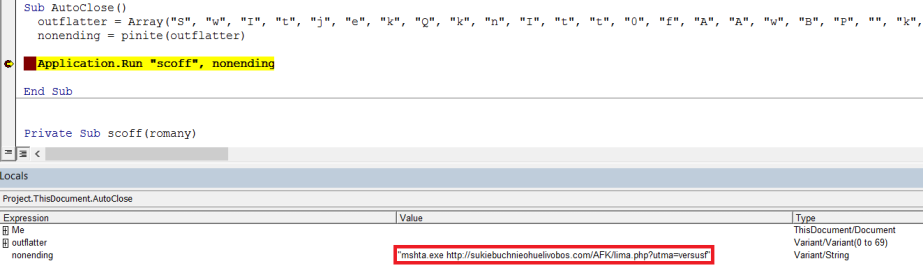
Dynamic analysis of the code via a debugger quickly shows the string we’re looking for:
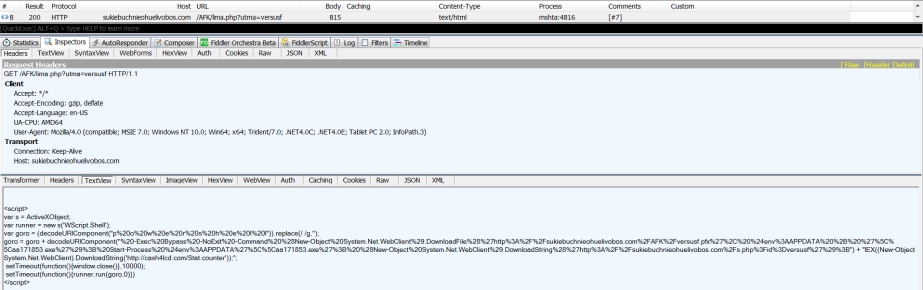
After closing the document, we can see the GET request to sukiebuchnieohuelivobos[.]com/AFK/lima.php?utma=versusf:
The User-Agent string used for this request was “Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 10.0; Win64; x64; Trident/7.0; .NET4.0C; .NET4.0E; Tablet PC 2.0; InfoPath.3)”. Furthermore, you can see the script returned by the remote server in the image above.
Decoding it shows the following PowerShell command:
The GET requests are shown below:
The GET request for sukiebuchnieohuelivobos[.]com/AFK/versusf.pfx returns the malware payload:
The GET request for sukiebuchnieohuelivobos[.]com/s.php?id=versusf simply returned “tid=versusf”.
The GET request for cash4lcd[.]com/Stat.counter returned the following command:
This generated the GET request for workswell[.]at/images/1300.exe:
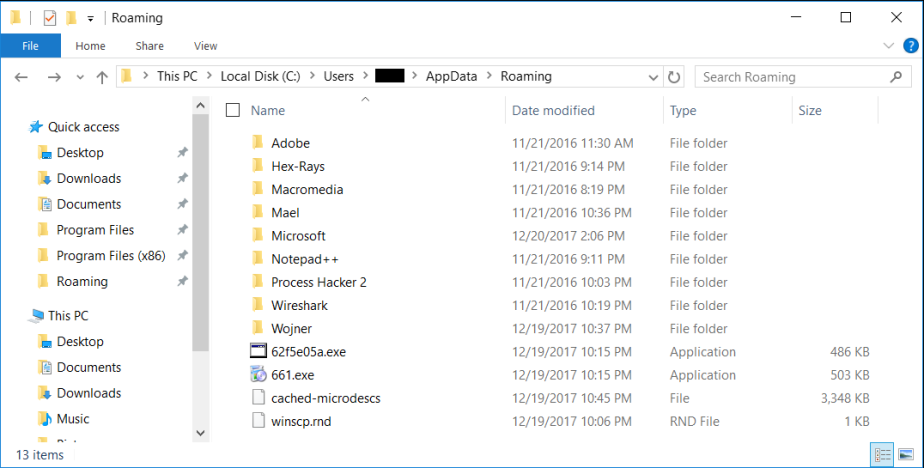
Both payloads were downloaded to %AppData% and then detonated:
For persistence, 661.exe sets autostart registry key “HKCUSOFTWAREMicrosoftWindowsCurrentVersionRunAppltdll:
Process 661.exe then created a copy of itself at “C:Users<User>AppDataRoamingMicrosoftBtpamResBthTtons.exe”:
661.exe creates a .bat file in a folder in %Temp%, writes to it, and then creates process cmd.exe. Process cmd.exe then reads from the .bat file, spawns cmd.exe as a child process, and then uses that to detonate BthTtons.exe. Process BthTtons.exe eventually deletes 661.exe.
Below is the process tree, which might give you a better understanding of what happened:
Post-infection traffic shows follow-up GET requests:
These GET requests appear to download files associated with the Tor functionality.
There is also this registry entry at HKCUSOFTWAREAppDataLowSoftwareMicrosoft:
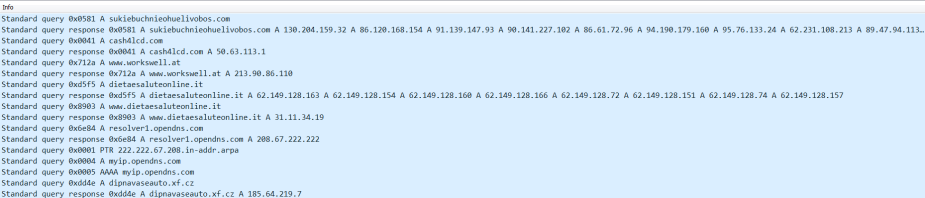
DNS queries and responses:
Some post-infection traffic:
More post-infection traffic found in the VT report:
Hashes:
SHA256: f0bdd862d6eced44b6f0a0a00681302994782275902c23a6be4baa1d4e98a8e6
File name: malspam.doc
Hybrid-Analysis report
SHA256: 041ad28cf8a6c03953910ea6dec3987ffd4daf729cce2a87e9bf68c480c0918e
File name: 62f5e05a.exe
Hybrid-Analysis report
SHA256: 0358ac37ad7a3bd29d19ff06d243666add9c2255bae1eb2bb32f0538440388c7
File name: 661.exe
Hybrid-Analysis report
Network Based IOCs:
- sukiebuchnieohuelivobos.com – GET /AFK/lima.php?utma=versusf
- sukiebuchnieohuelivobos.com – GET /AFK/versusf.pfx
- sukiebuchnieohuelivobos.com – GET /s.php?id=versusf
- cash4lcd.com – GET /Stat.counter
- 50.63.113.1
- http://www.workswell[.]at – GET /images/1300.exe
- 213.90.86.110
- http://www.dietaesaluteonline[.]it – GET /api/456.bin
- 62.149.128.154
- 62.149.128.163
- 31.11.34.19
- dipnavaseauto.xf.cz – GET /p.png
- 185.64.219.7
- mogolik.at – GET /assets/images/[removed]/C_2F_2Bm.jpeg
- 47.74.224.19
- mogolik.at – POST /assets/images/[removed]/_2BHk.gif
- 47.74.224.19
- classypetshop.com – GET /include/p1.pif
- 67.211.205.198
Files:
Password is “infected”
References:
https://threatpost.com/ursnif-banking-trojan-spreading-in-japan/128643/












[…] Gozi-ISFB is a variant of Ursnif, and today’s traffic looked like an example shared by @DynamicAnalysis in a blog post on malwarebreakdown.com. […]
LikeLike
[…] Gozi-ISFB is a variant of Ursnif, and today’s traffic looked like an example shared by @DynamicAnalysis in a blog post on malwarebreakdown.com. […]
LikeLike