Some security researchers on Tuesday had noted that their requests for the Seamless gates were failing. However, if there was any noticeable stoppage, it certainly didn’t last very long. Shortly after hearing about this I started checking my logs for any exploit kit activity and, as usual, I found a detection for RIG EK from one of our Palo Alto firewalls. Checking the traffic before the RIG EK detection showed the culprit to be the Seamless campaign.
Here is an example of the infection chain that I found:
Ad -> 193.124.xxx.xxx/vnc-seller -> 193.124.xxx.xxx/vnc-seller/ -> paremated-conproxy[.]com -> 15cen.redirectvoluum[.]com -> 194.58.xxx.xxx/signu1.php
The redirection chain that I found hasn’t changed much, however, this is the first time I’ve seen requests for /vnc-seller and /vnc-seller/. This could have had something to do with the geo-location of the host or the HTTP referer.
Other notable changes include the addition of the domain paremated-conproxy[.]com and the subdomain 15cen.redirectvoluum[.]com. They had been using the subdomains tqbeu.voluumtrk[.]com and tqbeu.redirectvoluum[.]com to redirect hosts to the Seamless gate.
The domain paremated-conproxy[.]com was first seen on 8/18/17. The Whois information is private. The subdomain 15cen.redirectvoluum[.]com was registered by CodeWise and was first seen on 08/21/17. They’re using CodeWise’s marketing suite called “Voluum“.
Furthermore, the Seamless .php file that returns the iframe pointing to the RIG EK landing page is now called signu[1-4].php rather than signup[1-4].php.
It was at this point that I decided to go hunting for my own infection.
The publisher that I used for my infection chain was another video streaming site. According to Alexa it is currently ranked in the top 69,000 globally and top 36,000 in the United States. Below is Alexa’s statistics on the site’s visitors by country:
| Country | Percent of Visitors | Rank in Country |
| United States | 27.20% | 35,100 |
| United Kingdom | 14.60% | 13,900 |
| India | 12.50% | 23,900 |
| South Africa | 4.60% | 7,500 |
| Australia | 3.80% | 19,100 |
Overall the site received roughly 340,000 visitors in the last 30 days.
Below is a flowchart from my infection:
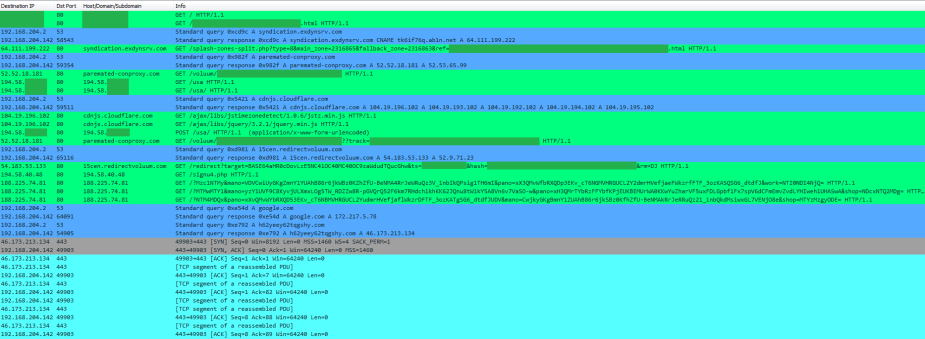
Below is an image of the HTTP, DNS, and C2 traffic filtered in Wireshark:
The Ramnit payload was dropped and detonated in %Temp%. We then see the malware copy itself to a new folder in %LocalAppData% where it was then executed.
Once the file is run from %LocalAppData% we see the first DNS query for Google.com. After successfully resolving Google.com comes the DNS query for the C2 domain h62yeey62tqgshy.com (resolves to 46.173.213.134). The infected host then initiated connections to the C2 server via TCP port 443.
During this same time, you see two more copies of the malware being dropped back into %Temp% as well as Ramnit’s .log files being created in various locations like %LocalAppData% and %ProgramData%:
This same beaconing pattern with Google.com and the C2 repeats itself over and over again:
We can also see that the malware creates various methods of persistence on the system, including creating a file in Startup and setting some values in the registry:
IOCs
Pre-infection:
194.58.40.48 – IP literal hostname used by the Seamless campaign
188.225.74.81 – IP literal hostname used by RIG EK
Post-infection:
DNS queries for h62yeey62tqgshy.com
Connections to 46.173.213.134 via TCP port 443
Hashes
SHA256: ff1184382121f67d04aafb09879bddbd449b1e95b2ca50933fce1574ffb84b50
File name: RigEK landing page from 188.225.74.81.txt
SHA256: cbf7dfc2226e592149ef45539c9a4f109c4e66533fe061037241fb88c245ce57
File name: RigEK Flash exploit from 188.225.74.81.swf
SHA256: 62687447bd28623e2a584e4c0e761b5ed365bfe057621523a29025d4210fcada
File name: o32.tmp
SHA256: 8995e321efc5cedbc979e43d9f7c84440b346573dbeb71b7a3c941052ad87428
File name: 949ideuf.exe
Hybrid-Analysis Report
Downloads
Seamless RigEK Ramnit Malicious Artifacts 082217.zip
Password is “infected”
Until next time!










[…] Pomimo zamknięcia trzystu serwerów C&C przez Europol w 2015, Ramnit nadal ma się dobrze. Ostatnio jest dystrybuowany za pomocą exploit-kita RIG EK z seamless gates. […]
LikeLike