On May 10th, 2017, the Twitter user thlnk3r sent a Tweet with a referer for the seamless campaign:
I decided to investigate the traffic from his tweet and proceeded to use the php file hosted at 185.31.160.55 as my referer. Here is the traffic from my run:
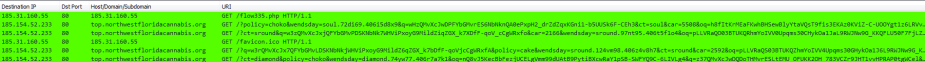
This tactic proved to be successful as I was redirected from 185.31.160[.]55/flow335.php to a RIG exploit kit landing page being hosted at the subdomain top.northwestfloridacannabis.org at 185.154.52.233:
As you can see from the TCP stream the GET request for flow335.php returned an iframe containing a URL for a RIG exploit kit landing page. It also contained the following string at the very bottom:
If you would like to make a link or bookmark to this page, the URL is: hxxp://sheldonbrown.com/web_sample1.htmlThe host is then sent the Flash exploit and the malware payload. The malware payload was dropped and executed in %Temp%:
The malware copies itself to %AppData% and creates some .log files:
It also creates a .log file in ProgramData (64 characters):
We also see it modify and set some values in the registry:
HKCUSoftwareAppDataLow[GUID]HKCUSoftwareMicrosoftWindowsCurrentVersionRunHKLMSoftwareMicrosoftWindows NTCurrentVersionWinlogonIt also writes to a start menu file:
I found my infected host making A LOT of ARP requests to IP addresses in its subnet. This traffic was followed by even more connection requests to host in the private address spaces via TCP port 110 (POP3). The POP3 requests caused the following ET rule to trigger:
- ET SCAN Rapid POP3 Connections – Possible Brute Force Attack
There was also another ET rule that triggered:
- ET SCAN Behavioral Unusual Port 139 traffic, Potential Scan or Infection
IOCs
HTTP Traffic:
- 185.31.160.55 – GET /flow335.php – Seamless campaign redirector
- 185.154.52.233 – top.northwestfloridacannabis.org – RIG EK
- VirusTotal report showing the full RIG EK URLs resolving to that IP address.
Post-infection traffic via TCP port 443:
- 95.215.108.213 – mudsaoojbjijj999.com
Hashes:
SHA256: 7bf27431646d969018fc9a168a23cafbc0f2602a6f6a206ede9e89bab9c428f6
File name: flow335.php.txt
SHA256: 45ba6629e0cd77f78047fc0c4a0bc7031294d4b2e9c71076e880050f9d6385f9
File name: top.northwestfloridacannabis.org RIG EK landing page.txt
SHA256: 0b993d0f76a4811a88d57138a8d7a22da15160d89724a9fa9ad34460629985a4
File name: RIG EK Flash Exploit 051017.swf
SHA256: 5183f7ac5c52f0077a78d27023f94bf5358a24b4e56cc78fc4897a5f715b0807
File name: o32.tmp
SHA256: 06cd9ab627fe1ff313634a7286bff48420d3ca466ad13da5935116e09ea4b29a
File name: mk9ls87v.exe
SHA256: d907cc78026032ab366f7762e2df7255a84ccf0352faa5ebaa941674052bcea5
File name: dwjkhvua.exe
Hybrid-Analysis Report
Malicious Artifacts (password is “infected”):
Malicious Artifacts 051017.zip
You can download the malware payload from VirusTotal or Hybrid-Analysis.
Until next time!











[…] @thlnk3r tweeted about Rig exploit kit (EK) activity. @DynamicAnalysis has already posted an analysis of this traffic on malwarebreakdown.com (always a good read), but Ive also looked into it. Today […]
LikeLike