IOCs:
- 88.214.225.168 – duckporno.com – Decoy site
- 80.77.82.42 – walterboroads.info – GET /rotation/hits? – Malicious redirect
- 194.87.144.170 – mail.mobildugun.com – RIG-v EK
Post-Infection Traffic:
- 94.23.186.184 – GET /images/[truncated]/MK/.avi – ET TROJAN Ursnif Variant CnC Beacon
- 94.23.186.184 – GET /tor/t32.dll – ET CURRENT_EVENTS Possible Malicious Tor Module Download
- 37.48.122.26 – curlmyip.net – GET for external IP
- Outbound connections via port 9001 – ET POLICY TLS possible TOR SSL traffic
DNS Queries:
- resolver1.opendns.com – ET POLICY OpenDNS IP Lookup
- 222.222.67.208.in-addr.arpa
- myip.opendns.com
- nod32.com
Traffic:
Hashes:
SHA256: 4bf2693a8e3567d73acafcf9e0b3c9f97ef941942d579a36a378ea4dcaa94d9f
File name: Walterboroads.info – rotation – hits.html
SHA256: 141456ee1e7ba00aae65d99ae46c9820a7810e831529608952348e74917ef394
File name: mail.mobildugun.com RIGv EK pre landing page.html
SHA256: 8786f7478d8bab62adceafda45f1a6d7f098ca2ab8ea3d29e5014695efa4ee4c
File name: mail.mobildugun.com RIGv EK landing page.html
SHA256: b3669ec83fb4bba5257da8c68b32dc15d1a08e9e8c22c7483698f29de2839b5f
File name: mail.mobildugun.com RIGv EK Flash exploit.swf
SHA256: beb0195000135671cda3b2428ce9b3601d47d56edfc72461cdbcee7bbc7b8862
File name: QTTYUADAF
SHA256: 7c69835f15b3ffd5f21dda086fd3835bea74569bbb0127d431e760979d11775d
File name: radB88AE.tmp.exe
Hybrid-Analysis Report
SHA256: 5d5bda87bb2871b29c63d7a40c3f7e1ef81ebb4c69396059e94d4ce02ece9f10
File name: t32.dll
SHA256: 844e63492bd90551aff973d093be4bf2610bbb3057b86fe1a146f7bc412cfa92
File name: B8E9.bin
Infection Chain:
This infection was basically identical to my last infection. Same domain, same iframe, similar payloads and similar post-infection traffic. Here is the iframe found on the compromised site:
Just like with my previous infection the iframe returned a page from the EK server that contained script meant to identify the browser. According to the library directory on the domains the script is called firstDetect.js.php:
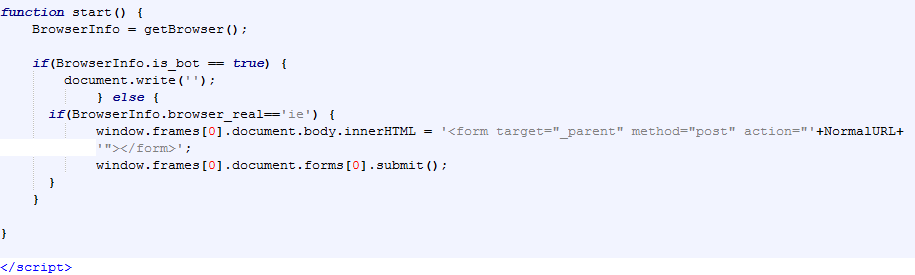
The host will be redirected to the value contained within the NormalURL if they are using IE. Below are partial images of the script which contains the URLs necessary for redirection:
This script also instructs the host to use the POST method when making the request. The server returns basically the same page:
Besides the URIs being different we see a difference with what is returned if BrowserInfo.is_bot == true. Examples are shown below:
It was at this point that the host made a second POST request using the URL found on the pre-landing page.
In the video you can see the location where the malicious code loaded. In my previous write up I got an interesting error loaded on the page:
Needless to say the GET request for the first malicious redirect, rotation/hits?, failed.
Moving on… Once the landing page loaded we see the host make a GET request for a Flash exploit and then the payload. The payload, radB88AE.tmp.exe, was dropped in my %Temp% folder and copied to a new folder in Roaming (dot3Core.exe):
Next we see the creation of folders B950 and FFFE, and files AC39.bi1 and B8E9.bin (Tor client). There are also numerous .bin files created as the system continues to run, along with a cached-microdescs file (used by the Tor client) created in Roaming:
There are also some modifications to the registry:
The last thing we see before the Tor traffic is a GET request for curlmyip.net, which is used to identify the external IP address being used by the host.
I recommend that SOC analysts filter network traffic over the last 72 hours or so and look for any communication to 80.77.82.42. You can correlate connections made to 80.77.82.42 with other suspicious activities, which would include Exploit Kit traffic and any anti-virus events.
Lastly, I would block 80.77.82.42, 94.23.186.184, and 194.87.144.170 at your perimeter firewall(s). Until next time!