Download location where I got the malicious Word document:
- 192.232.223.76 – kinonah.com – GET /Cust-4762868855/ – Compromised website hosting malicious Word document
- VirusTotal Report
- Hybrid-Analysis Report
- SHA256: d8cfe351daa5276a277664630f18fe1e61351cbf3b0a17b6a8ef725263c0cab4
Additional Word document download locations:
- 213.190.161.210 – avenueevents.co.uk/Cust-PBP-03-D683320/
- 67.212.91.221 – kingstoncybermall.com/Cust-3647227423/
- 5.10.105.46 – theuntoldsorrow.co.uk/ORDER.-XI-80-UY913942/
- 173.236.177.156 – visuals.com/CUST.-VT-38-RH422386/
- 192.254.251.86 – thenursesagent.com/ORDER.-9592209302/
- 192.185.148.240 – tiger12.com/TGA-48-76252-doc-May-04-2017/
- 192.185.216.220 – gabrielramos.com.br/lxu-3h-ip079-zgmg.doc/
- 146.185.16.121 – britbuys.co.uk/MMQKS-13-50456-doc-May-04-2017/
- 186.233.185.77 – bbcinfo.com.br/Cust-Document-OR-23-D181969/
- 212.1.208.253 – kineticwebdesign.co.uk/ORDER.-0674979321/
- 192.185.88.17 – hand-ip.com/Cust-Document-5777177439/
- 67.227.229.37 – bobrow.com/ito-6r-w193-pkr.doc
- 81.169.145.158 – wyskocil.de/ORDER-525808-73297/
- 192.254.231.89 – citylifeevents.co.uk/ORDER.-1198574243/
- 146.185.181.231 – proiecte-pac.ro/ORDER.-5883789520/
- 85.25.226.200 – zypern-aktiv.de/wp-content/plugins/wordfence/Cust-0396638436/
- 66.7.193.7 – sublevel3.us/Cust-5226149026/
- 205.204.94.16 – forthtechnologies.com/CUST.-Document-SHO-10-K839208/
- 66.198.240.165 – highbeamshoes.com/Cust-XNG-91-EO055424/
- 5.249.147.247 – itgastaldi.com/CUST.-Document-QGU-29-Z264146/
- 67.227.212.192 – wlrents.com/CUST.-Document-YDI-04-GQ389557/
- 89.187.85.6 – redkitecottages.com/Cust-Document-VMH-46-TJ804065/
- 173.236.147.244 – thegilbertlawoffice.com/m-9q-d054-gu.doc/
- 65.39.128.43 – sheyana.com/ORDER.-Document-8187485601/
- 192.185.73.127 – gregbenjamin.com/CUST.-Document-TIJ-37-J534842/
Geodo/Emotet download locations:
- 209.97.242.26 – dynamat.com/tou1yn-sq755-x/
- 69.163.152.76 – sheacorp.com/ism3qo-u416-kjdd/
- 74.55.90.58 – bullridemania.com/vs9r-z679-yg/
- 144.208.69.18 – melodywriters.com/um5tc-c110-srd/
- 79.96.237.135 – masil.pl/gfx/mhl7mcv-hb478-qy/
- VirusTotal Report
- Hybrid-Analysis Report
- SHA256: b254d81796eb96329c14797bc43e4fbf62eb08c4eb21afea084b425bc867c5b9
Additional Geodo/Emotet download locations:
- 148.251.213.108 – arrowlink.com/uk1ej-kt757-md/
- 80.150.6.143 – stromkontor.org/b8hcg-o392-gj/
- 192.185.145.58 – danmichaelis.com/uf1t-g513-xa/
- 143.95.238.54 – mmaacombatzone.com/wse9o-jr465-pguf/
C2s:
- 81.88.24.211:443
- 87.106.189.18:8080
- 66.175.215.16:8080
- 103.219.22.63:443
- 139.59.33.202:8080
- 50.116.5.69:443
- 62.210.36.193:8080
- 62.75.181.217:8080
- 74.50.57.220:8080
- 75.25.153.57:443
- 79.170.95.202:7080
- 87.106.148.126:443
- 92.51.129.235:443
- 78.47.56.162:443
Secondary downloads:
- 72.249.55.86 – incadesc.com.mx/dephm8uabdpkb83arcml/
- VirusTotal Report
- Hybrid-Analysis Report
- SHA256: a56498a062e95f7030ed92b740716004bf3433d3107daed1c2082b08aa1040ad
Infection Chain:
My infection chain didn’t begin with the email. Instead, I had an alert in a SIEM from a Wildfire event catching return HTTP traffic from hand-ip.com/Cust-Document-5777177439/ at 192.185.88.17. The return HTTP traffic was attempting to deliver the malicious Word document to the internal host. While I didn’t receive the malspam it would seem as though they’re sending out phishing emails with malicious links that point to the malicious Word documents being hosted on various compromised websites.
I decided to download the Word document to see what was going on. Once I downloaded the Word document I opened it and was presented with the familiar social engineering tricks of enabling editing and then enabling content:
Once the user enables both editing and content their host will make GET requests for the malware payload being hosted on numerous compromised websites. Below is an example of network traffic up to this point:
The Hybrid-Analysis report for the Word document shows the processes and the PowerShell script used to download the malware:
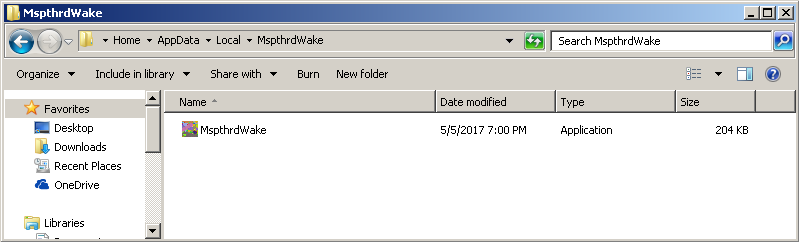
The malware payload is dropped in %Temp% and then moves itself to %AppData% under a random folder:
MspthrdWake’s .lnk file is created inside the Startup folder in the system Start Menu so it can automatically run whenever the system starts:

Ealier versions would use HTTP POST requests containing the encrypted data to the C2 server. However, newer variants are using GET requests to send the encrypted data within a Base64 encoded cookie string:
The C2 server responds with a fake “404 Not Found” status; however, the body is full of encrypted data.
During one of my infections I also noticed another GET requests for incadesc.com.mx/dephm8uabdpkb83arcml/. This delivered the file “3658854804.exe”:

Around the same time I got this executable I noticed another user on Twitter mention it as well:

The other executable, “103171900.exe”, scanned clean on VirusTotal. File details shows it to be autoconv.exe from Auto File System Conversion Utility by Microsoft Corporation.
Here is some of the C2 GET requests traffic filtered in Wireshark:
Download the malicious Word document (password is infected):
All the other files can be downloaded via the Hybrid-Analysis reports.
Until next time!
References:
- http://blog.fortinet.com/2017/05/03/deep-analysis-of-new-emotet-variant-part-1
- https://blogs.forcepoint.com/security-labs/new-variant-geodoemotet-banking-malware-targets-uk
- https://www.cyphort.com/emotet-cookies-c2-fakes-404/
- https://www.cisecurity.org/emotet-changes-ttp-and-arrives-in-united-states/
- https://myonlinesecurity.co.uk/open-the-attachment-to-view-the-document-malspam-delivers-a-multitude-of-malware/









The autoconv.exe is an evasion tactic by the malware. Basically if it decides based on some criteria it is being analysised or sandbox it runs something like “cmd.exe /c ping.exe -n 6 127.0.0.1 & type “%WINDIR%\System32\autoconv.exe” > “C:\114443363.exe” to overwrite itself. Check out these hybrid-analysis records.
Infected Word Doc:
https://www.hybrid-analysis.com/sample/c28aa0ddc6bdc5c7c34e2634d6f1d73aac0527cf3b512cfb4a611817bc6870b3?environmentId=100
First EXE it dropped:
https://www.hybrid-analysis.com/sample/c2d3856c203245f0849b52d46fb25f5b4ffc7b2a031e61b5141bde6fb2bbc8e0?environmentId=100
Second EXE it dropped:
https://www.hybrid-analysis.com/sample/de3b0d40b3a8ce8be51c831d980d916293b3c14f13b719f99123bc907790791b?environmentId=100
Open the infected word doc and away it went.
Emotet stole the local credentials (Chrome Auto-Complete) from the device, stashed them in a .tmp file in the %appdata% folder and transmitted them.
The second EXE started trying what must have been a dictionary attack against the active directory accounts on the network.
I submitted both EXEs to hybrid-analysis and malwar, but the EXEs just overwrote themselves with autoconv.exe both times rather than executing their payload.
LikeLiked by 1 person
Correction I guess, looks like he malware that stole the credentials was Emotet version E AKA “Heodo” apparently the successor of Geodo / Emotet.
LikeLiked by 1 person
Hey,
Thank you for the detailed information!
LikeLike
[…] earlier, we didnt obtain a copy of the email with a link to the Word document. Last month, a similar report on Emotet was published on malwarebreakdown.com, but it was also without an example of the associated emails. […]
LikeLike
I was sent a very similar package by my local city recycling utility today. It seems that their email system got infiltrated and the malicious word doc was sent as an attachment to customers who recently submitted customer service requests. The macro was written in French!
LikeLike
[…] unique feature of this malware is that it exploits a built-in feature in MSWord. Whenever a Word file is opened, this feature automatically updates any links contained in the […]
LikeLike
[…] from Eastern Europe over the past two years. Among its dubious customers are groups that operate QakBot, Dridex, IcedID and […]
LikeLike
[…] methods in 2017, serving elite cybercrime groups from Eastern Europe, such as those operating QakBot and Dridex. It has now added IcedID as a new payload drop. Emotet emerged in 2014 after a […]
LikeLike